Recently, I have often seen that some people are discussing POS machine cleaning machine and second cleaning machine. Some people probably know what it means, but they will still be a bit dazed. The following small series will give you a science popularization of what is a machine, what is two Clearance, if not clear, will eat a lot of losses.
First of all, a clearing machine, a clearing machine means that the merchant settlement funds directly hit the account bound by the POS machine merchant through UnionPay or a third-party payment platform, without going through other accounts in the middle, having their own independent background, there is an official Backstage. The flow path of funds when settlement: Consumer (swipe) → UnionPay (or third-party payment platform) → Collection account (to account), it looks very simple, it is three steps, there are no other extra steps, not only fast , still safe.
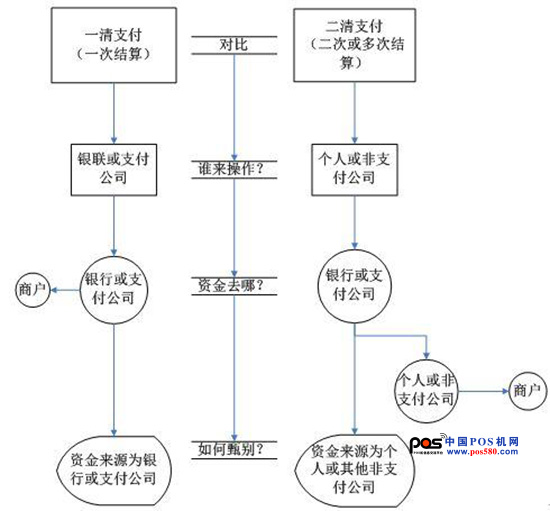
Then I said that the second cleaning machine, the second cleaning machine is an ordinary company that does not have a bank card acquiring business. They apply for multiple POS machines with their own company qualifications, and take one of them to the merchants. The funds are advanced to their company accounts, they pass Manually re-established to the card merchants, there may be a lot of POS machines in the middle, and the frequently seen set code and code hopping phenomenon also occur on the second cleaning machine. The flow path of funds when settlement: Consumer (swipe card) → UnionPay (or third-party payment platform) clearing center → third-party account → collection account (to account).
Does it look a little dizzy? It doesn't matter, a picture makes you really understand
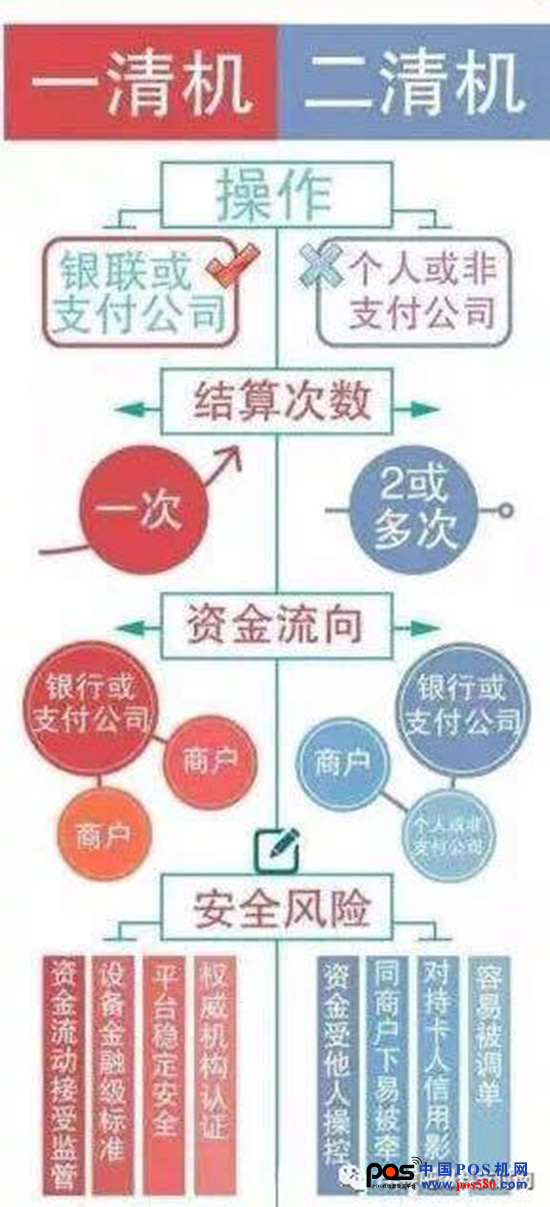
In particular, it can be seen that there is no problem with a cleaning machine. Is the second cleaning machine not good? In fact, there is a very serious problem in the second cleaning machine, because it is necessary to go through a third-party account, so it is very likely that there will be a phenomenon that the third party will run after getting the money. This is also why it is very dangerous to use the second cleaning machine. If you want to use the second cleaning machine, you still have to go to the agent of the regular agent second cleaning machine to buy, do not find an agent without qualification.
So how do you separate your own POS machine into a clean machine or a second clean machine? In fact, there are several convenient ways:
1. The main difference between a cleaning machine and a second cleaning machine is the settlement step. If the arrival time is late, it is very likely that it is a second cleaning machine, but it does not rule out some cleaning machines. It is good to use a clearing machine certified by UnionPay;
2, see if there is an independent background, a clear machine with an official independent background, support real-time query transaction details, through the official customer service check business license information and settlement account information can accurately distinguish whether it is a clear machine, if there is no independent background Must be the second machine of the POS machine;
3. See who is the banker. If the bank card with the bank card has online banking, log in directly to the online banking and see the transaction details. If the party is a third-party payment platform that pays the license, it is a clearing machine. It is a personal or general company that is the second cleaning machine, if there is no online banking to the counter to print the transaction list.
In this year's credit card fraud case, two of them were fraudulent through “no card paymentâ€. Fan, a reporter who studied abroad, returned to China and found that his credit card was paid 20,000 RMB, but Fan did not spend it abroad during his return. It is very likely that Fan’s credit card information was stolen by criminals during his study abroad, and then it was used for on-site consumption through some third-party payment platforms outside the country, and then resold cash.

The so-called "cardless payment" (ie "fast payment") means that consumers only need to enter the credit card number and expiration date, CVV verification code to complete the payment when shopping on non-physical channels such as telephone or online, without using the card. Physical ontology, some need to enter a password, some do not need a password, that is, the highest risk of no card and no confidential payment, and the latter is the mainstream way of "no card payment". The traditional credit card fraud pseudo-card crimes are realized by making fake cards. With the development of Internet commerce and electronic payment methods, the "no card payment" method of "convenience" is rapidly emerging and accepted by the public. .
One is to purchase overseas email account and password cash.
The criminal gang buys the overseas email account and password from the Internet, and uses the same APP account to scan the software to scan whether the email account has applied for the APP account. At the same time, if the credit card is bound to the APP account, as long as the APP account password is known, the online account can be directly paid without the need to input the credit account and password. The leased Apple mobile phone determines whether the APP account is bound through the wireless network. A credit card. If it is bound, the proxy server will be connected to the Internet store to purchase the game equipment or game card currency of the specific game abroad, and then organize the staff to sell the game equipment or game to the domestic and foreign game players through Taobao and other channels. The currency is thus cashed out.
The second is to purchase overseas credit card information cash.
The criminal gang buys overseas credit card information from the Internet (mainly the following four items of credit card information: card number, card owner name, expiration date, credit card CVV verification code), and then uses the leased Apple mobile phone to pass the wireless network proxy. The server pretends to be the IP address of the credit card attribution, links to the Apple online store, sets the Apple store account, and bundles the overseas credit card information, purchases the game equipment or game card currency that the game player likes in the Apple online store, and then resells it to the middleman to cash out. The sale of criminal suspects and intermediaries is achieved through QQ contact, and the proceeds are transferred by the intermediary through Alipay.
By understanding the criminals' use of the above two modus operandi, they remind the masses to pay attention to protecting personal information and avoid disclosure. In addition to speed, we must also be vigilant and avoid the loss of personal property.
Kitchen Cleaning Tool,Reusable Household Glove,Disposable Kitchen Cleaning Cloths,Rubber Dishwashing Gloves
vchomy , https://www.ivchomy.com