introduction
With the development of computer and network technology, e-commerce, enterprise & ' (, e-mail and other network services have been actively promoted in all walks of life, including corporate e-mail services are the most widely used, and most familiar with users. Mail The service has a long history. Due to the limitations of the environment at the time, the security concept was not considered too much when designing the architecture. As a result, most of the enterprise mail system structures are relatively simple and there are many security risks. The storage and transmission process is based on plain text. The only security mechanism is the management of user access rights. Network intruders can easily intercept or invade the mail server to steal important email information through the network.
In order to solve the security problems of mail storage and transmission, data encryption, digital signature, etc., security technologies such as %, !* have been applied to the enterprise mail system. While these techniques ensure that messages are ciphertext-based during transmission and storage, security issues for encrypting messages and digitally signing keys are not addressed. At present, these keys are basically stored in the mail receiving terminal or the central server. With the development of network attack technology, the method of saving the user key thus poses a serious threat to the security of the mail system. The smart card not only stores sensitive information such as keys, certificates, and user data, but also ensures that the hardware level of the confidential information is protected from tampering, and the data can be encrypted, decrypted, signed, and verified for signature operations in the card. This paper proposes an enterprise secure mail system based on smart card technology. The system introduces smart card technology in the mail receiving and dispatching terminal to ensure the security of confidential information such as keys, and effectively solves the encryption, decryption, signature and verification process of the existing mail system. Security issue.
Related technology
Mail service system
At present, a large part of the information of enterprises is transmitted through the mail service of the office automation system, which is usually based on (standard Internet mail service of the agreement) or the internal network mail service based on database technology.
For the standard Internet mail service based on (the protocol is to use the store-and-forward mechanism for transmission, but the title and content of the message are based on plaintext throughout the transmission process, the security problem is: on the one hand, the attacker It is possible to obtain sensitive information through network interception; on the other hand, mail temporarily stored on the mail server is also likely to be stolen by an attacker. Based on the path of the mail transmission in the standard Internet mail service of the agreement, the user is shown. The mail is written by the user agent, and then the agent sends the mail to the local mail transfer server, and the local mail server transmits to the server of the other user 2 through a certain route; the user 2 can retrieve the mail from the server through the agent. The mail so that the user 2 can read the mail. It can be seen that the open network environment poses a serious security threat to the transmission and storage of the mail.
For the internal network mail service based on database technology, the process of sending and receiving mail is as shown in the figure. This architecture is very suitable for large-volume enterprise-level mail service, and has the advantages of high speed and high stability. However, in addition to the network monitoring security threats in the transmission process, the security risks still exist in the operating system of the mail server or the vulnerability of the database system itself and the negligence in configuration. The title and content of the message are stored in the database in clear text. Once the attacker hacks into the database system, the content will be completely under the control of the attacker.
.jpg)
Security solutions for existing mail systems
Messages in plain text are not secure during transmission and storage. Such security issues can be resolved by encrypting the message. If symmetric key encryption is used, assuming that the number of enterprise mail system users is n, then the entire enterprise needs to maintain "a key, which is suitable in the case of a small number of users, but in the enterprise environment, the number of users is very large, so that The daily maintenance, update, and release of keys is very labor intensive.
.jpg)
Although the asymmetric key encryption technology ensures that the mail is ciphertext based on the transmission and storage process, the security problem for encrypting the mail and digitally signing the key is not solved. At present, these keys are basically stored in the mail receiving terminal or the central +, server. With the development of network attack technology, the method of saving the user key thus poses a serious threat to the security of the mail system.
Smart card technology
A smart card is a combination of hardware and software developed for a specific application. It can securely store sensitive information such as keys, certificates, and user data to prevent tampering at the hardware level of confidential information. In many applications, the smart card chip can independently perform security-sensitive computing tasks such as encryption, decryption, identity authentication, and digital signature, thereby improving the application system against virus attacks and preventing the leakage of sensitive information.
At the heart of a smart card is a microchip that includes the processor, memory, operating system, and firmware. It can be understood as a computer system without specialized input and output devices. According to its different internal hardware and software architecture, it can be subdivided into the following four types:
Memory card: It is only a simple storage device, and can not perform corresponding card calculation. It cannot be applied in an application environment with security requirements.
Encrypted memory card: Adds encryption processing logic based on the stored information, which can encrypt the information in the card.
CPU card: With processor and memory, it can not only store information, but also perform complex encryption and decryption operations on data. The card's autonomic computing power has significantly improved the security of the card's information.
RF card: RF transceiver circuit is added on the basis of CPU card to realize contactless read and write operations.
Enterprise Secure Mail System Based on Smart Card Technology
Mail security
Although the existing secure mail system implements the process of encrypting and decrypting mail and signing and verifying the mail, it solves the security problem of the mail during storage and transmission. However, with the development of the network attack technology, it is absolutely safe for the user to hold the private key. The assumption is no longer satisfied: computer resources are currently shared in many enterprises. If the user stores the private key on the client, this will make it easy for other users sharing the computer to access the private key; if the user's private key is used Stored on a central server, due to system vulnerabilities or configuration negligence, the user's private key may be leaked, which makes the existing secure mail system face serious security threats. To solve this problem, the most important thing is to ensure the absolute security of the user's private key. For this reason, the author introduces a smart card with autonomic computing function in the terminal of the system to realize the hardware level of the user's private key to prevent tampering. The smart card is managed by a unified card issuer in combination with the user's identity information, so that the original secure mail system model has a very solid security guarantee without changing the architecture.
.jpg)
In the mail sending process of Figure 6, the processing step in the gray box is that the mail sender encrypts the mail content summary processing result with the private key. This step is processed within the smart card, and the result is returned to the external mail agent after encryption. In this way, the external program cannot directly access the user's private key, so that the security of the private key can be guaranteed to the greatest extent. The previous encryption process is performed by an external mail agent, which first obtains the public key of the mail recipient from the %& server, and then encrypts the key. Since the user's public key is public, external encryption on the smart card can make full use of the resources of the external client, increase the encryption speed, and the security will not be reduced.
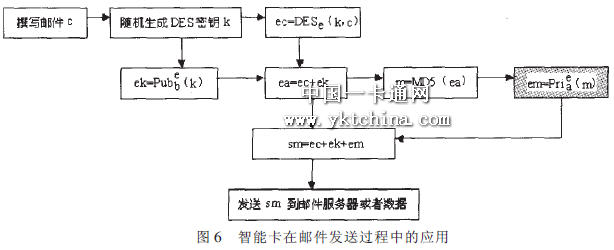
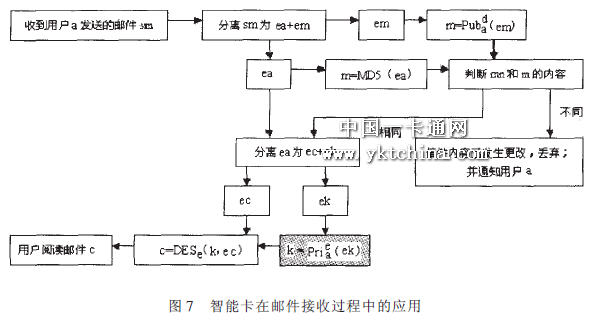
In the mail receiving process flow of the figure, the gray box indicates the process of decrypting the private key by the mail recipient. The external mail agent will be sent to the smart card, decrypted by the card to get the key, and returned to the external mail agent. The decryption process of the mail is implemented on the external client, and the mail agent is directly prevented from directly accessing the user's private key. Improve overall system efficiency and safety.
Key management
Key management mainly includes the management and maintenance of public keys, private keys and certificates. The user's private key is stored in the smart card held by the user. It is generated by the card issuing program when the card is issued, and the user's public key data is also generated and stored in the company's %& server, when the user needs it. It can be obtained from the server. The public key data on the server is used by all enterprise users, and the security requirements are low, so it can be solved by the security of the operating system and database system. In addition, if a user's smart card is lost, the user's certificate should be revoked when the user loses the smart card, so that a certificate revocation list needs to be maintained on the server to control the certificate recovery. The enterprise is also responsible for the issuance and management of the smart card. The private key is directly written into the smart card held by the user after the generation, and the card issuing institution does not save the copy, thus ensuring the security of the mail system to the greatest extent.
Model implementation
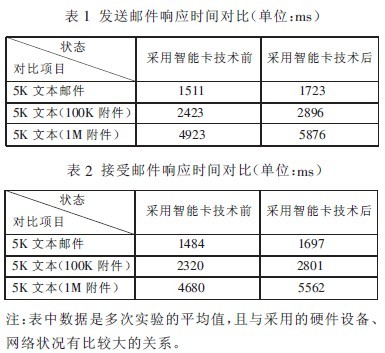
The design features of the model have been programmed and embedded in an office automation system. This fully solves the problem of the original system in terms of information security, and is also recognized in terms of ease of use. To process a daily work email, the response time of the system can be found in the table.
By comparison, it can be seen that in the mail system, the model described in the article is used to process the mail, and the security is guaranteed, and the performance of the loss is acceptable. This proves that the proposed model algorithm is combined, a large amount of mail data is decrypted, and a small amount of sensitive information is very effective in the idea of ​​encryption and decryption in the smart card by 2) & algorithm.
in conclusion
The importance of the mail system in the enterprise office automation platform has been recognized by everyone, and the transmission and storage technology of the mail service is still very fragile in terms of security. It is necessary to implement a secure mail service in the enterprise, encrypting and signing the mail. It is essential. This paper proposes an enterprise security email system based on smart card technology. The system introduces smart card technology in the mail receiving and dispatching terminal to ensure the security of confidential information such as keys, minimize the security risks of the system, and encrypt and decrypt the mail. Signature and verification signatures effectively solve the security problem of mail storage and transmission without changing the original mail system architecture.
Cross stitch is practiced from ancient embroidery, revealing the breath of wealth. "Family and everything are prosperous" has always been the eternal pursuit of Chinese people. It symbolizes the harmony of the family. The use of 5D diamond material shows the prosperity of a family. Diamond Painting new living room cross stitch deer full diamond 5d point paste diamond masonry crystal handmade masonry.
Diamond Painting,5d Diamond Painting,Point Drill Painting, Diy Diamond Painting
Dongguan Junkai Packaging Products Co., Ltd , https://www.diystoragecases.com